GNS3
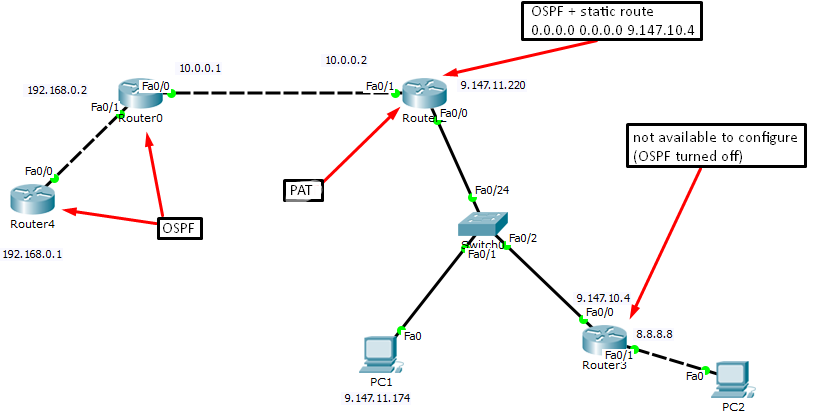
1. В GNS3 собрал схему:
Роутер подсоединен к облаку (интернет раздается с LAN-карты ноута в GNS). Пинг от роутера до ноута не проходит (файрвол выключен). Но и роутер и ноутбук пингуют 10.147.6.40 ( default GW ноута). К тому же в arp таблицах они есть друг у друга (ноут и роутер).
-arp -a
-show arp
This is a really old reply to a really old post but I finally found a solution to this mess. I too couldn't ping my virtual cisco pix running in GNS3 from my host (Windows 7 32 bit). In XP I could. What I finally realized was that even wireshark was reporting bad checksums. After some heavy digging I ran into this wiki on the wireshark site http://wiki.wireshark.org/CaptureSetup/Offloading. Ladies and gentlemen TCP, UDP, and IP checksumming being offloaded to the nic card is killing us all. Cool feature but something that really F's up WinPCAP. If the OS is no longer doing the packet checksums it appears to all software using WinPCAP that the packet is bad and it just drops. As soon as I disabled this feature on my laptop so that the OS does the checksumming again everything works great again. SNORT also suffered from this issue which is why I'm heading to their support forum next. On my machine to turn off Offloading I did the following: In Windows, go to
Control Panel->Network and Internet -> Network and Sharing Center, click Local Area Connection Link of the connection to change then choose 'Properties' button. Press the 'Configure...' button, choose the 'Advanced' tab to modify the "IP V4 Checksum Offload" and "TCP Checksum Offload (IPV4)" and "UDP Checksum Offload (IPV4)". I changed the setting from RX and TX Enable to Disabled
so that the OS will compute the checksum. Note: I had to reboot my machine after the setting changes. Hope this works for you as it did for me!
2. NAT (чтоб сделать доступ из приватной сети в публичную)
Router1>enable Router1#configure terminal
Create a NAT pool of global addresses
Router1(config)#ip nat pool mypool 10.147.6.10 10.147.6.15 netmask 255.255.255.248
Create a standard access control list that permits the addresses that are to be translated
Router1(config)#access-list 1 permit 192.168.93.128 0.0.0.15
Establish dynamic source translation, specifying the access list that was defined in the prior step
Router1(config)#ip nat inside source list 1 pool mypool overload
This command translates all source addresses that pass access list 1, which means a source address from 192.168.93.128 to 192.168.93.141, into an address from the pool named mypool (the pool contains addresses from 10.147.6.10 to 10.147.6.15)
Overload keyword allows to map multiple IP addresses to a single registered IP address (many-to-one) by using different ports
The question said that appropriate interfaces have been configured for NAT inside and NAT outside statements.
This is how to configure the NAT inside and NAT outside, just for your understanding:
Router1(config)#interface fa0/0
Router1(config-if)#ip nat inside
Router1(config-if)#exit
Router1(config)#interface s0/0
Router1(config-if)#ip nat outside
Роутер подсоединен к облаку (интернет раздается с LAN-карты ноута в GNS). Пинг от роутера до ноута не проходит (файрвол выключен). Но и роутер и ноутбук пингуют 10.147.6.40 ( default GW ноута). К тому же в arp таблицах они есть друг у друга (ноут и роутер).
-arp -a
-show arp
This is a really old reply to a really old post but I finally found a solution to this mess. I too couldn't ping my virtual cisco pix running in GNS3 from my host (Windows 7 32 bit). In XP I could. What I finally realized was that even wireshark was reporting bad checksums. After some heavy digging I ran into this wiki on the wireshark site http://wiki.wireshark.org/CaptureSetup/Offloading. Ladies and gentlemen TCP, UDP, and IP checksumming being offloaded to the nic card is killing us all. Cool feature but something that really F's up WinPCAP. If the OS is no longer doing the packet checksums it appears to all software using WinPCAP that the packet is bad and it just drops. As soon as I disabled this feature on my laptop so that the OS does the checksumming again everything works great again. SNORT also suffered from this issue which is why I'm heading to their support forum next. On my machine to turn off Offloading I did the following: In Windows, go to
Control Panel->Network and Internet -> Network and Sharing Center, click Local Area Connection Link of the connection to change then choose 'Properties' button. Press the 'Configure...' button, choose the 'Advanced' tab to modify the "IP V4 Checksum Offload" and "TCP Checksum Offload (IPV4)" and "UDP Checksum Offload (IPV4)". I changed the setting from RX and TX Enable to Disabled
so that the OS will compute the checksum. Note: I had to reboot my machine after the setting changes. Hope this works for you as it did for me!
2. NAT (чтоб сделать доступ из приватной сети в публичную)
Router1>enable Router1#configure terminal
Create a NAT pool of global addresses
Router1(config)#ip nat pool mypool 10.147.6.10 10.147.6.15 netmask 255.255.255.248
Create a standard access control list that permits the addresses that are to be translated
Router1(config)#access-list 1 permit 192.168.93.128 0.0.0.15
Establish dynamic source translation, specifying the access list that was defined in the prior step
Router1(config)#ip nat inside source list 1 pool mypool overload
This command translates all source addresses that pass access list 1, which means a source address from 192.168.93.128 to 192.168.93.141, into an address from the pool named mypool (the pool contains addresses from 10.147.6.10 to 10.147.6.15)
Overload keyword allows to map multiple IP addresses to a single registered IP address (many-to-one) by using different ports
The question said that appropriate interfaces have been configured for NAT inside and NAT outside statements.
This is how to configure the NAT inside and NAT outside, just for your understanding:
Router1(config)#interface fa0/0
Router1(config-if)#ip nat inside
Router1(config-if)#exit
Router1(config)#interface s0/0
Router1(config-if)#ip nat outside

Comments
Post a Comment