CISCO NAT
To go to the Internet we need to get an public IP address and it is
unique all over the world. If each host in the world required a unique
public IP address, we would have run out of IP address years ago. But by
using Network Address Translation (NAT) we can save tons of IP
addresses for later uses. We can understand NAT like this:
“NAT allows a host that does not have a valid registered IP address to communicate with other hosts through the Internet”
For example your computer is assigned a private IP address of 10.0.0.9 and of course this address can not be routed on the internet but you can still access the internet. This is because your router (or modem) translates this address into a public IP address, 123.12.23.1 for example, before routing your data into the internet. Of course when your router receives a reply packet destined for 123.12.23.1 it will convert back to your private IP 10.0.0.9 before sending that packet to you.
Maybe you will ask “hey, I don’t see any difference of using NAT to save tons of IP addresses because you still need a public IP address for each host to access the Internet and it doesn’t save you anything, why you need to use NAT?”
Ok, you are right :), in the above example we don’t see its usefulness but you now understand the fundamental of NAT!
Let’s take another example!
Suppose your company has 500 employees but your Internet Service Provider (ISP) only gives you 50 public IP addresses. It means that you can only allow 50 hosts to access the internet at the same time. Here NAT comes to save your life!
One thing you should notice that in real life, not all of your employees uses internet at the same time. Say, maybe 50 of them use internet to read newspaper at the morning; 50 others use internet at noon for checking mail… By using NAT you can dynamically assign these 50 public IP addresses to those who really need them at that time. This is called dynamic NAT.
But the above NAT solution does not solve our problem completely because in some days there can be more than 50 people surfing web at the morning. In this case, only the first 50 people can access internet, others must wait to their turns.
Another problem is, in fact, your ISP only gives you much lesser IP addresses than the number 50 because each public IP is very precious now.
To solve the two problems above, another feature of NAT can be used: NAT Overload or sometimes called Port Address Translation (PAT)
PAT permits multiple devices on a local area network (LAN) to be mapped to a single public IP address with different port numbers. Therefore, it’s also known as port address translation (PAT). When using PAT, the router maintains unique source port numbers on the inside global IP address to distinguish between translations. In the below example, each host is assigned to the same public IP address 123.1.1.1 1 but with different port numbers (from 1000 to 1002).
NAT terms:
* Inside local address – The IP address assigned to a host on the inside network. The address is usually not an IP address assigned by the Internet Network Information Center (InterNIC) or service provider. This address is likely to be an RFC 1918 private address.
* Inside global address – A legitimate IP address assigned by the InterNIC or service provider that represents one or more inside local IP addresses to the outside world.
* Outside local address – The IP address of an outside host as it is known to the hosts on the inside network.
* Outside global address – The IP address assigned to a host on the outside network. The owner of the host assigns this address.
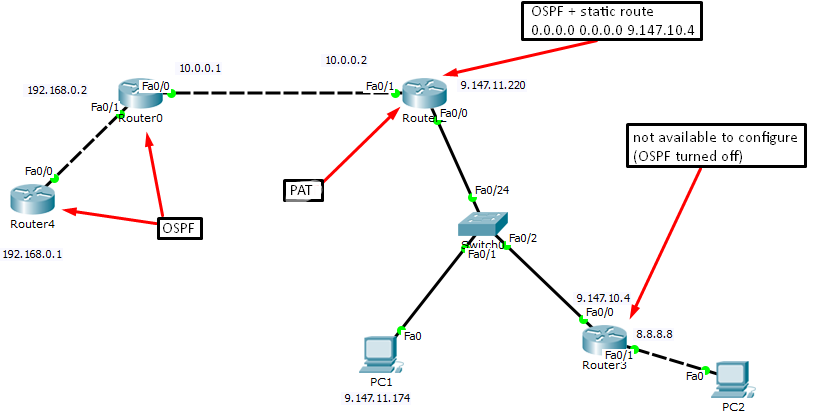
Настройка static NAT
Одному внешнему адресу соответствует один внутренний
1. проверяем пинг между и нтерфейсами самого роутера, чтоб понять проходит ли пинг с одного интерфейса (внутреннего f0/0) на другой (внешний f0/1)
R1:
en
∟ping
∟Target IP address: 9.147.11.220
Extended commands [n]: yes
∟ Source address or interface: 10.0.0.2
Пинга конечно нет, так как мы пытаемся пинговать с внутренней сети во внешнюю

Настроим static NAT на R1:
en
∟conf t
∟ip nat inside source static 10.0.0.2 9.147.11.220
∟int f0/0
∟ip nat inside
∟int f0/1
∟ip nat outside
Мы создали правило, которое преобразует ip 10.0.0.2 в 9.147.11.220. Теперь пинг между интерфейсами будет, мы так же можем теперь пинговать с 10.0.0.2 адрес 9.147.10.4. Но если мы хотим, чтоб пинг от R0 проходил до R2, то нам надо писать новое правило, которое преобразует 10.0.0.1 в 9.147.11.221 (потому что 9.147.11.220 уже занят). В этом неудобство
Настройка dynamic NAT (ограничение в 50 адресов)
на R1:
1) создаем пул с адресами
en
∟conf t
∟ip nat pool MYNATPOOL 9.147.11.221 9.147.11.230 netmask 255.255.255.0
2) создаём ACL с локальными адресами, которым надо дать внешние адреса:
∟ access-list 1 permit 10.0.0.0 0.0.0.255
3) привязываем локальные адреса (ACL) к внешним (к Pool'у)
∟ip nat inside source list 1 pool MYNATPOOL
4) вешаем NAT на интерфейсы
∟int f0/0
∟ip nat inside
∟int f0/1
∟ip nat outside
Настройка PAT/NAT overload
на R1:
1) Пул с адресами можно не создавать, так как адрес у нас всего один
2) создаём ACL с локальными адресами, которым надо дать внешние адреса:
en
∟conf t
∟ access-list 1 permit 10.0.0.0 0.0.0.255
3) привязывать локальные адреса (ACL) к внешнему интерфейсу
∟ip nat inside source list 1 interface fa0/0 overload
4) вешаем NAT на интерфейсы
∟int f0/0
∟ip nat inside
∟int f0/1
∟ip nat outside
“NAT allows a host that does not have a valid registered IP address to communicate with other hosts through the Internet”
For example your computer is assigned a private IP address of 10.0.0.9 and of course this address can not be routed on the internet but you can still access the internet. This is because your router (or modem) translates this address into a public IP address, 123.12.23.1 for example, before routing your data into the internet. Of course when your router receives a reply packet destined for 123.12.23.1 it will convert back to your private IP 10.0.0.9 before sending that packet to you.
Maybe you will ask “hey, I don’t see any difference of using NAT to save tons of IP addresses because you still need a public IP address for each host to access the Internet and it doesn’t save you anything, why you need to use NAT?”
Ok, you are right :), in the above example we don’t see its usefulness but you now understand the fundamental of NAT!
Let’s take another example!
Suppose your company has 500 employees but your Internet Service Provider (ISP) only gives you 50 public IP addresses. It means that you can only allow 50 hosts to access the internet at the same time. Here NAT comes to save your life!
One thing you should notice that in real life, not all of your employees uses internet at the same time. Say, maybe 50 of them use internet to read newspaper at the morning; 50 others use internet at noon for checking mail… By using NAT you can dynamically assign these 50 public IP addresses to those who really need them at that time. This is called dynamic NAT.
But the above NAT solution does not solve our problem completely because in some days there can be more than 50 people surfing web at the morning. In this case, only the first 50 people can access internet, others must wait to their turns.
Another problem is, in fact, your ISP only gives you much lesser IP addresses than the number 50 because each public IP is very precious now.
To solve the two problems above, another feature of NAT can be used: NAT Overload or sometimes called Port Address Translation (PAT)
PAT permits multiple devices on a local area network (LAN) to be mapped to a single public IP address with different port numbers. Therefore, it’s also known as port address translation (PAT). When using PAT, the router maintains unique source port numbers on the inside global IP address to distinguish between translations. In the below example, each host is assigned to the same public IP address 123.1.1.1 1 but with different port numbers (from 1000 to 1002).
NAT terms:
* Inside local address – The IP address assigned to a host on the inside network. The address is usually not an IP address assigned by the Internet Network Information Center (InterNIC) or service provider. This address is likely to be an RFC 1918 private address.
* Inside global address – A legitimate IP address assigned by the InterNIC or service provider that represents one or more inside local IP addresses to the outside world.
* Outside local address – The IP address of an outside host as it is known to the hosts on the inside network.
* Outside global address – The IP address assigned to a host on the outside network. The owner of the host assigns this address.
Настройка static NAT
Одному внешнему адресу соответствует один внутренний
1. проверяем пинг между и нтерфейсами самого роутера, чтоб понять проходит ли пинг с одного интерфейса (внутреннего f0/0) на другой (внешний f0/1)
R1:
en
∟ping
∟Target IP address: 9.147.11.220
Extended commands [n]: yes
∟ Source address or interface: 10.0.0.2
Пинга конечно нет, так как мы пытаемся пинговать с внутренней сети во внешнюю

Настроим static NAT на R1:
en
∟conf t
∟ip nat inside source static 10.0.0.2 9.147.11.220
∟int f0/0
∟ip nat inside
∟int f0/1
∟ip nat outside
Мы создали правило, которое преобразует ip 10.0.0.2 в 9.147.11.220. Теперь пинг между интерфейсами будет, мы так же можем теперь пинговать с 10.0.0.2 адрес 9.147.10.4. Но если мы хотим, чтоб пинг от R0 проходил до R2, то нам надо писать новое правило, которое преобразует 10.0.0.1 в 9.147.11.221 (потому что 9.147.11.220 уже занят). В этом неудобство
Настройка dynamic NAT (ограничение в 50 адресов)
на R1:
1) создаем пул с адресами
en
∟conf t
∟ip nat pool MYNATPOOL 9.147.11.221 9.147.11.230 netmask 255.255.255.0
2) создаём ACL с локальными адресами, которым надо дать внешние адреса:
∟ access-list 1 permit 10.0.0.0 0.0.0.255
3) привязываем локальные адреса (ACL) к внешним (к Pool'у)
∟ip nat inside source list 1 pool MYNATPOOL
4) вешаем NAT на интерфейсы
∟int f0/0
∟ip nat inside
∟int f0/1
∟ip nat outside
Настройка PAT/NAT overload
на R1:
1) Пул с адресами можно не создавать, так как адрес у нас всего один
2) создаём ACL с локальными адресами, которым надо дать внешние адреса:
en
∟conf t
∟ access-list 1 permit 10.0.0.0 0.0.0.255
3) привязывать локальные адреса (ACL) к внешнему интерфейсу
∟ip nat inside source list 1 interface fa0/0 overload
4) вешаем NAT на интерфейсы
∟int f0/0
∟ip nat inside
∟int f0/1
∟ip nat outside



Comments
Post a Comment